Tag: authentication
-

More on Data Security
In continuing with our discussion of security components that are critical to Cloud or On-Premise (Enterprise) applications, Data Security has to be among the top issues for ELN and LIMS systems. In the ELN market, “data” is information stored in many different formats, from files to databases on many different devices from network servers, personal…
-
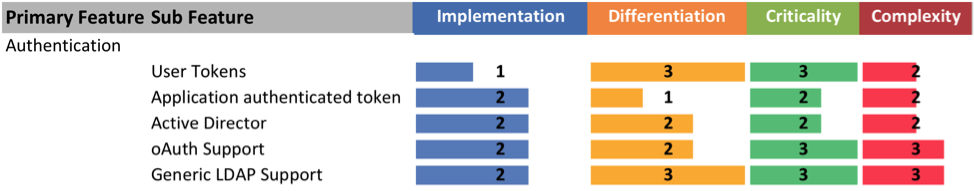
Using Scorecards to Rank Security Needs
Last week we briefly discussed the fact that security means different things to different people depending on their job function, point-of-view, or context. Often a purchase decision needs cross-functional teams comprised of the different stakeholders affected when evaluating Enterprise or Cloud Software security solutions. What good does it do for IT to mandate a system because…
