CERF is the only ELN currently available that offers true PKI hashing of your digital signatures, offering the most non-repudiable 21 CFR 11 compliant protection of your Intellectual Property.
Title 21 – Part 11 of the U.S. Code of Federal Regulations, often abbreviated 21 CFR Part 11 or even just 21CFR11, stipulates the legal requirements for all electronic records subject to inspection by the U.S. Food and Drug Administration. Although the regulation grew out of the need to establish guidelines for the authentication of computerized records to be used in lieu of paper records by the pharmaceutical industry, 21 CFR 11 is considered an “umbrella regulation” that applies to all of the industries overseen by the FDA, including food production and cosmetics. Moreover, 21 CFR 11 has been used as the model for GLP, GCP, and GMP regulations around the globe.
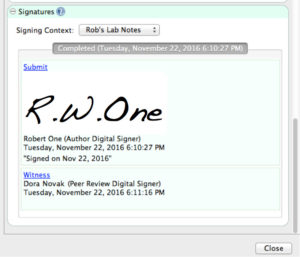
A primary focus of this code is to clarify “the criteria under which the agency considers electronic records, electronic signatures, and handwritten signatures executed to electronic records to be trustworthy, reliable, and generally equivalent to paper records and handwritten signatures executed on paper.” Given the emphasis on tightly controlled digital signatures, CERF–the only available ELN with true PKI hashing to encrypt signatures–stands head-and-shoulders above other scientific data management systems for compliant laboratories.
In fact, every notebook entry in the company’s CERF system is a set of separate records, each with its own MD5 hash digest. This value is stored with each record to detect content changes. CERF’s workflow signs each of the records in the set, uniquely applying the U.S. federal government’s Digital Signature Algorithm (DSA).
What is and is not 21 CFR 11 compliant:
It is important to note that the regulation applies to electronic records–including the policies by which they are created, updated, signed, and eventually archived–and thus is not strictly a computer system regulation. Because compliance includes specific policies and procedures carried out by the users of the ELN, no computer system can be deemed 21 CFR 11 compliant by itself; instead, all such systems must be validated in situ, ideally by a third party. As a vital part of your regulated operations, CERF ELN has been designed to meet or exceed all required controls that apply to the environment housing your scientific data. The chart below explains how CERF ELN complies with all applicable clauses of the code.
Lab-Ally works with several partners who can assist you with independent validation in situ of your CERF system. Contact us when you are ready to get started.
To download a PDF version of the 21CFR11 Compliance chart for CERF below, click here.
Lab-Ally has created a slideshow presentation summarizing the 21CFR11 content on this page, see below.
CERF ELN, 21CFR11 Analysis and Compliance from Lab-Ally LLC
Subpart B – Electronic Records
| § Number | Code Language | Compliance | Description |
| 11.10 | Controls for closed systems. | ||
| 11.10 | Persons who use closed systems to create, modify, maintain, or transmit electronic records shall employ controls designed to ensure the authenticity, integrity and, when appropriate, the confidentiality of electronic records, and to ensure that the signer cannot readily repudiate the signed record as not genuine. Such procedures and controls shall include the following: |  CERF is Compliant CERF is Compliant | CERF provides security controls, audit trails and a digital signature system to ensure the authenticity, integrity and confidentiality of records. The CERF system only accepts records and document updates from authorized users who supply suitable credentials in authenticated sessions. CERF security administration ensures only authorized users can access, update, create or add document information, assuring the authenticity of a document. Record integrity is achieved by providing a complete audit trail and version history, including a copy of the previous and updated record, which can only be accessed by authorized users. CERF offers robust role-based access controls, ensuring highly granular permissions that can restrict unauthorized users from viewing or accessing documents, providing complete confidentiality of records. The CERF user authentication controls, digital signature passwords and signature workflows, and the matching audit trail collectively ensure that the signer can not readily repudiate the signing or the signed electronic record. |
| 11.10(a) | Validation of systems to ensure accuracy, reliability, consistent intended performance, and the ability to discern invalid or altered records |  CERF is Compliant CERF is Compliant | CERF is an electronic lab notebook system for managing lab records and research content. We validate our system to ensure that it performs reliably and consistently for its intended uses, and that that the content and records in the system are maintained accurately and reproducibly. Actions that create, modify, or delete records are recorded in a secure, computer-generated audit trail. Hash codes and true, PKI-based digital signatures are stored in the database and can be used to discern invalid or altered records. Thorough and systematic testing to validate the performance of CERF is conducted with every release cycle and with each customer installation. |
| 11.10(b) | The ability to generate accurate and complete copies of records in both human readable and electronic form suitable for inspection, review, and copying by the agency. Persons should contact the agency if there are any questions regarding the ability of the agency to perform such review and copying of the electronic records. |  CERF is Compliant CERF is Compliant | CERF was designed specifically to enable research organizations to manage scientific content and records in electronic forms that support both reuse of the original formats (data/document objects) and human readable and printable formats suitable for recordkeeping, including inspection, review, and copying by the FDA and other agencies. CERF accomplishes the generation of accurate and complete copies in two ways. The original electronic records are readable, reviewable, and capable of being copied directly within the operating CERF software system by anyway with suitable credentials. For system-independent and software-independent use, CERF can create PDF versions of text and non-text resources for export or printing, as well as PDF reports of all related metadata for any resource including entire notebooks, notebook pages and folders. These PDF records are stored in the system and are readily retrieved, printed, or transferred to other storage systems. PDF is intended to offer a long-term solution for maintaining copies of records in human readable and electronic form suitable for inspection, review and copying. Individual electronic records can also be copied to desktop applications for these purposes. CERF also supports exports of complete notebooks (with full contents, records, and metadata) in open standard XML format. |
| 11.10(c) | Protection of records to enable their accurate and ready retrieval throughout the records retention period. |  CERF is Compliant CERF is Compliant | Records are protected by restricting access to authorized users and preventing any unauthorized changes. Users cannot directly modify or delete records in CERF – all actions are mediated by the CERF Server, a secure middle tier which prevents direct access to data. CERF offers a complete document/record control system with system locks when records are checked out for editing, maintenance of all versions of lab records, and the capability to finalize lab records to restrict any further changes. Accurate records are accessible and retrievable throughout their lifecycle in CERF. All versions of all resources are kept forever and never removed from CERF unless the system administrator allows it. |
| 11.10(d) | Limiting system access to authorized individuals. |  CERF is Compliant CERF is Compliant | The CERF administration program provides an exceptional level of system security. All users must be registered in the system by qualified system administrators, and users are given unique user names and user-designated passwords (that must be changed by the user when assigned or reset by the administrator). CERF has strong name/password controls, and passwords are transmitted only in encrypted form and not stored on the server (only a digital hash code). Users are placed into defined workgroups and have specific, fine-grained role-based access privileges within these workgroups. All records and content in CERF are assigned to workgroups (at the object level as specified directly or as inherited from parent nodes, as set by those given managerial control of workgroups). Users may be in multiple workgroups such that they have different privileges in different projects/notebooks and even different limits on access to templates, actions, and services as well as to the content. Users without minimal (read only) access cannot even view records, while a minimal level of ‘Annotator’ is required to add notes and links to records, ‘Editor’ is needed to be able to check out and edit documents, and ‘Notebook Editor’ role is needed to be able to create or modify the contents of CERF lab notebooks. When users successfully log on to CERF, unique session IDs are created and transmitted with every system communication to prevent inappropriate access. Simultaneous sessions (from multiple workstations) are not permitted for a user, and connecting from a different computer or from more than one CERF application simultaneously will end the older session. |
| 11.10(e) | Use of secure, computer-generated, time-stamped audit trails to independently record the date and time of operator entries and actions that create, modify, or delete electronic records. |  CERF is Compliant CERF is Compliant | The CERF system includes a complete audit trail function that captures all actions that create, modify or delete data. Audit trails are secure, computer-generated and time-stamped. Recorded fields include creation date and time, update date and time, user name, object modified (by name and system resource object type), action taken, reason (where appropriate), and the new content and metadata. A complete copy of the previous record and its metadata is retained in the system if the content has been placed under version control. The audit trail can be viewed in the CERF web client by authorized CERF administrators, and the database can be queried to generate custom audit trail reports. The audit trail is independent of the database entries for each record, and can be compared to verify that user actions and lab records have been documented correctly. |
| 11.10(e) – continued | Record changes shall not obscure previously recorded information. |  CERF is Compliant CERF is Compliant | Documents, data, and notebook entries must be checked out before any changes can be made. Records are locked when contents are checked out. On checking in, the file is stored as a new version, with previous versions stored in the CERF system. The previous version of the metadata is also retained with its record. The version history may be inspected and previous record versions viewed by authorized users. |
| 11.10(e) – continued | Such audit trail documentation shall be retained for a period at least as long as that required for the subject electronic records and shall be available for agency review and copying. |  CERF is Compliant CERF is Compliant | CERF audit trail records are maintained in the database and can be viewed or extracted from the system directly or through queries for the functional life of the software system. The audit trail information cannot be deleted or modified from within the CERF system. The audit trail documentation is available for agency review, and reports can be made for inspection or copying. |
| 11.10(f) | Use of operational system checks to enforce permitted sequencing of steps and events, as appropriate. |  CERF is Compliant CERF is Compliant | All actions that create, modify, or delete records occur inside CERF. All actions are operational sequences performed by users authorized to carry out the function and system workflows which verify the events, data management workflows, and the validity of the data and records. CERF actions are defined and limited by the CERF system components and business policies, and are distributed to individuals automatically and securely by the system according to the type of system object, the user’s role-based access privileges, and the services available for the selected object. The workflows and actions in CERF are defined by ontologies which cannot be changed by end-users, and templates, which can only be created and modified by users with an appropriate role. CERF utilizes internal controls at every step of processes that create or manipulate records to ensure that only appropriate actions and steps of action sequences and workflows are permitted. Such controls include adding new content and annotations to collections (such as Projects and Notebooks), signature workflows, editing and checking in lab records, and validating fields for metadata entry. |
| 11.10(g) | Use of authority checks to ensure that only authorized individuals can use the system, electronically sign a record, access the operation or computer system input or output device, alter a record, or perform the operation at hand. |  CERF is Compliant CERF is Compliant | CERF contains security checks to ensure that only authorized and assigned individuals can view, access, create, and modify records. The system requires that an operator has an active CERF account and has logged in with a valid user name and password before any actions can be taken. Once logged in (and until manual or system initiated logout or timeout), a session identifier is passed with every user action to ensure that the operation is specified by the authenticated user. System checks restrict a user from carrying out any action that not authorized for a specific user within a specific workgroup on a specific object/record of a specific type and state (for example, version controlled or finalized). Allowable CERF actions are offered to the operator as dynamically created, context-dependent menus and tool bars. Inappropriate actions cannot be specified (such inputs are not made available in the interface) and would be rejected by the CERF server if somehow delivered (such as if record status changed immediately after selection of an action). Workflows such as digital signatures require that an authorized user with an active CERF session selects a record that the user has contributed to CERF, with requirements that the record is in a signable state, and that the record is owned by a workgroup for which the signer has required co-signers available (if needed) and that the user enters a valid signature password. CERF provides authority checks throughout user operation of the software, including all actions that add or modify records or signatures. If available actions or user access rights change during CERF operation, the effects will be propagated to the user and thereby modify or deny access or other privileges and actions. |
| 11.10(h) | Use of device (e.g., terminal) checks to determine, as appropriate, the validity of the source of data input or operational instruction. |  CERF is Compliant CERF is Compliant | CERF can be configured to accept data or other instructions only from specific locations. CERF utilizes the same controls as for user operation, such as requiring an instrument user name and password to create an active session, and additional checks, such as validation of data in transit and device IP address requirements. The user organization is responsible physical security of devices and workstations. |
| 11.10(i) | Determination that persons who develop, maintain, or use electronic record/ electronic signature systems have the education, training, and experience to perform their assigned tasks. |  CERF is Compliant CERF is Compliant | Lab-Ally staff and developers undergo rigorous, ongoing training. Lab-Ally maintains up-to-date documentation for all aspects of the deployment, configuration and use of the CERF ELN system. Lab-Ally offers a full suite of training services for customer admins and end users in operation of the CERF software, and can make recommendations on recordkeeping and electronic signature practices. The customer organization is responsible for ensuring that its users have appropriate training and experience to perform their assigned tasks, including maintaining lab records and signing their lab notebooks. |
| 11.10(j) | The establishment of, and adherence to, written policies that hold individuals accountable and responsible for actions initiated under their electronic signatures, in order to deter record and signature falsification. |  CERF is Compliant CERF is Compliant | Lab-Ally offers a full suite of training services for customer admins and end users. This training includes both product usage recommendations and guidance to organizations for how to optimize their system and internal processes for maximum compliance and security. Although ultimately ensuring proper training of all users is the customer’s responsibility, we work with customers as needed to make sure minimum industry standards are met. The client organization is responsible for developing and following written policies (SOPs) for electronic signatures, CERF signature workflows and lab recordkeeping practices. |
| 11.10(k) | Use of appropriate controls over systems documentation including: |  CERF is Compliant CERF is Compliant | Lab-Ally provides standard CERF system documentation, including documents for system administration, user operation, release notes, as well as versioned documentation on system modifications from one software release to the next. |
| 11.10(k)(1) | Adequate controls over the distribution of, access to, and use of documentation for system operation and maintenance. |  CERF is Compliant CERF is Compliant | Lab-Ally provides system administration documentation to the client. Documentation on the CERF system is distributed by Lab-Ally only as appropriate to authorized individuals with appropriate role/ permissions. The client is responsible for disseminating or controlling access within their organization to operational and maintenance documents, and also for managing system passwords for administrators. |
| 11.10(k)(2) | Revision and change control procedures to maintain an audit trail that documents time-sequenced development and modification of systems documentation. |  CERF is Compliant CERF is Compliant | Lab-Ally records are maintained in our own, internal CERF instance, with full audit trail and version controls, for maximum security and compliance. Lab-Ally supplies new system operation and administration documents and release notes with its installation and updates of CERF. The client organization is responsible for maintaining records and audit trails for any CERF system, CERF component, or policy changes that are made to its system. |
| 11.30 | Controls for open systems Persons who use open systems to create, modify, maintain, or transmit electronic records shall employ procedures and controls designed to ensure the authenticity, integrity, and, as appropriate, the confidentiality of electronic records from the point of their creation to the point of their receipt. Such procedures and controls shall include those identified in 11.10, as appropriate, and additional measures, e.g., document encryption and use of appropriate digital signature standards to ensure, as necessary under the circumstances, record authenticity, integrity, and confidentiality. |  CERF is Compliant CERF is Compliant | CERF is generally considered a closed system and can even be deployed in a completely sealed local network with no internet connectivity, if necessary. However, CERF does support all the necessary procedures and controls for managing electronic records in an open system, including encryption of documents and all communications between the client machine and the server. |
| 11.50 | Signature manifestations | ||
| 11.50(a) | Signed electronic records shall contain information associated with the signing that clearly indicates all of the following: (1) The printed name of the signer; (2) The date and time when the signature was executed; and (3) The meaning (such as review, approval, responsibility, or authorship) associated with the signature. |  CERF is Compliant CERF is Compliant | Signed electronic records in CERF contain the full printed name of signer, date/time when the signature was executed, the meaning of the signature, the role of the signer, and any comments provided by the signer. The system administrator can configure various signature roles, such as Submitter, Peer Reviewer (Witness), Manager/Approve, and Legal/Regulatory acceptance. The CERF administrator can also configure various signature workflows (for example, a single witness for Project documents, a manager approval for lab SOPs, and two witnesses and a manager for lab notebook pages). User authority for signatures can be restricted to specific roles, documents/records and work events. |
| 11.50(b) | The items identified in paragraphs (a)(1), (a)(2), and (a)(3) of this section shall be subject to the same controls as for electronic records, and shall be included as part of any human readable form of the electronic record (such as electronic display or printout) |  CERF is Compliant CERF is Compliant | Electronic signature records are fully secure from unauthorized access, and can be displayed or printed for any electronic record. Notebook printing can be configured to meet the signature requirements of the client. |
| 11.70 | Electronic signatures and handwritten signatures executed to electronic records shall be linked to their respective electronic records to ensure that the signatures cannot be excised, copied, or otherwise transferred to falsify an electronic record by ordinary means |  CERF is Compliant CERF is Compliant | Once a digital signature (a PKI digital signature in CERF) is applied to a lab notebook page/entry, file object, or other CERF resource, an irrevocable link is established between the signature and the object. The digital signature cannot be deleted, copied or otherwise transferred to falsify the electronic record. A Lab-Ally PKI digital signature is cryptographically based on the object contents and cannot be falsified or tampered with, nor can the object signed be modified without invalidating the digital signature. |
Subpart C- Electronic Signatures
| § Number | Code Language | Compliance | Description |
| 11.100 | General requirements | ||
| 11.100(a) | Each electronic signature shall be unique to one individual and shall not be reused by, or reassigned to, anyone else |  CERF is Compliant CERF is Compliant | CERF enforces the uniqueness of each user ID/password combination, and further requires an additional Digital Signature password. The signature cannot be reused or reassigned to anyone else, even after the original user id has been deactivated or is no longer active. The private key used to generate the digital signature is unique and not known or accessible to anyone else. |
| 11.100(b) | Before an organization establishes, assigns, certifies, or otherwise sanctions an individual’s electronic signature, or any element of such electronic signature, the organization shall verify the identity of the individual. | Not Applicable | This is dependent upon the operational controls and procedures established at the client. It is the client organization’s responsibility to verify the identity of its CERF users and to maintain and submit records for each user certifying that their electronic signatures (digital signatures) in CERF are intended to be the legally binding equivalent of traditional handwritten signatures. |
| 11.110(c) | Persons using electronic signatures shall, prior to or at the time of such use, certify to the agency that the electronic signatures in their system, used on or after August 20, 1997, are intended to be the legally binding equivalent of traditional handwritten signatures. (1) The certification shall be submitted in paper form and signed with a traditional handwritten signature, to the Office of Regional Operations (HFC-100), 5600 Fishers Lane, Rockville, MD 20857. (2) Persons using electronic signatures shall, upon agency request, provide additional certification or testimony that a specific electronic signature is the legally binding equivalent of the signer’s handwritten signature. | Not Applicable | This is dependent upon the operational controls and procedures established at the client. It is the client organization’s responsibility to verify the identity of its CERF users and to maintain and submit records for each user certifying that their electronic signatures (digital signatures) in CERF are intended to be the legally binding equivalent of traditional handwritten signatures. Any additional requirements, certifications, or testimonies regarding an organization’s use of digital signatures is the responsibility of the client. Lab-Ally can assist its clients in planning and implementing digital signatures policies and practices. We work with customers as needed to make sure training in these procedures is provided and minimum industry standards are met. |
| 11.200 | Electronic signature components and controls | ||
| 11.200(a)(1) | Electronic signatures that are not based upon biometrics shall: Employ at least two distinct identification components such as an identification code and password. |  CERF is Compliant CERF is Compliant | CERF employs a model that requires a unique user id and password combination for general CERF system access (for the thick client software or the web interface). Users must be logged into CERF using this pair of credentials and have an authorized active CERF session in order to be able to electronically sign a document or record. Then, a third identification component, a digital signature password, is required to complete the signing process. |
| 11.200(a)(1)(i) | When an individual executes a series of signings during a single, continuous period of controlled system access, the first signing shall be executed using all electronic signature components; subsequent signings shall be executed using at least one electronic signature component that is only executable by, and designed to be used only by, the individual. |  CERF is Compliant CERF is Compliant | To execute a series of signings, a CERF user must first create an authorized user session by supplying a unique combination of user id and password. During a single, continuous period of controlled system access, the user may then sign numerous or multiple documents, resources, or other lab records by using the third electronic signature component, known only to the signer, which is the digital signature password. |
| 11.200(a)(1)(ii) | When an individual executes one or more signings not performed during a single, continuous period of controlled system access, each signing shall be executed using all of the electronic signature components. |  CERF is Compliant CERF is Compliant | Each time an individual executes signings not performed during a single, continuous period of controlled system access, the user must first be authenticated by the CERF server with the two signature components of unique user id and password. Then, once authorized, the user may execute one or more electronic signatures with the third signature component, the digital signature password. Any break in the controlled system access – whether manual or automatic – terminates the user session and requires all signature components in order to execute additional electronic signatures. |
| 11.200(a) | Electronic signatures shall: (2) Be used only by their genuine owners; and (3) Be administered and executed to ensure that attempted use of an individual’s electronic signature by anyone other than its genuine owner requires collaboration of two or more individuals. |  CERF is Compliant CERF is Compliant | Executing an electronic signature in CERF requires a unique combination of user id and password plus a third component, the digital signature password. When a system administrator adds a new user or resets a password, the CERF user must change the password before being able to create a new user session. The login password is therefore known only to the individual user, and not to the administrator or to other users. The individual is also responsible for creating or updating the digital signature password, which is encrypted and not known to the administrator or other users. Furthermore, it is actually the private digital signature key that is used to sign lab records, and this key is not known to anyone (it is generated from a DSA KeyPairGenerator and that generator is supplied with the key size and a randomly generated seed value). CERF electronic signatures are administered and executed to ensure that the only way anyone other than the genuine owner of the could sign with the individual’s electronic signature is for a system administrator to collaborate with another user and to supply that other user with signature components (user id and password) so that this other user could log in and change the rightful user password and then update the digital signature password, and then finally, while supplying all the credentials of the genuine owner, execute a signature. In CERF, these activities would be logged. It is each user’s responsibility to protect and not share user and digital signature passwords. |
| 11.200(b) | Electronic signatures based upon biometrics shall be designed to ensure that they cannot be used by anyone other than their genuine owners | Not Applicable | Use and maintenance of biometric devices and software is outside the scope of the CERF system. Lab-Ally will advise its clients on the use of such methods for signatures, and may offer customized solutions for use of biometrics for electronic signatures. As a best practice, Lab-Ally recommends the configuring the appropriate business policy in CERF to use passwords of not less than 15 characters and use of strong passwords. These can be stored in modern password tools such as Bitwarden that have their own separate biometric features. |
| 11.300 | Controls for identification codes/ passwords. Persons who use electronic signatures based upon use of identification codes in combination with passwords shall employ controls to ensure their security and integrity. Such controls shall include |  CERF is Compliant CERF is Compliant | CERF provides robust controls for use of identification codes/passwords in electronic signatures. These controls ensure the security and integrity of digital signature identification components in CERF. |
| 11.300(a) | Maintaining the uniqueness of each combined identification code and password, such that no two individuals have the same combination of identification code and password. |  CERF is Compliant CERF is Compliant | Uniqueness of each user id and password combination is enforced – no two individuals may have the same user id in CERF. CERF business policies also control the required complexity of the password, such as password length and the number of non-alphabetic characters required. |
| 11.300(b) | Ensuring that identification code and password issuances are periodically checked, recalled, or revised (e.g., to cover such events as password aging) |  CERF is Compliant CERF is Compliant | Password aging is fully supported by CERF. System business policies specify the frequency of required password renewals (every thirty days is a common setting). The user is first challenged to re-enter the current password before submitting a new password that must be different, meet organizational requirements for password complexity, and be entered twice identically in order for the password to be accepted. |
| 11.300(c) | Following loss management procedures to electronically deauthorize lost, stolen, missing, or otherwise potentially compromised tokens, cards, and other devices that bear or generate identification code or password information, and to issue temporary or permanent replacements using suitable, rigorous controls. | Not Applicable | CERF does not use identification devices. However, the CERF administrator has authority to disable user accounts and to reset passwords. Users are required to modify their passwords immediately on login following a password reset. |
| 11.300(d) | Use of transaction safeguards to prevent unauthorized use of passwords and/or identification codes, and to detect and report in an immediate and urgent manner any attempts at their unauthorized use to the system security unit, and, as appropriate, to organizational management. |  CERF is Compliant CERF is Compliant | CERF offers several transaction safeguards to prevent unauthorized use, or attempted use, of the software. CERF can be set by the administrator to disable an account after a configurable number of incorrect logins. For security, only the administrator can re-enable the account for the genuine owner. Administrators can also specify a time-out period of inactivity after which a log-out is forced automatically by the system; after this, a user must login again with user id and password to create a new user session. A common time-out setting is thirty minutes. If a user is known to be gone for a long period, the account can be temporarily inactivated by the administrator, thus preventing any system access or electronic signatures associated with the user id of that individual. As another safeguard, CERF prevents any user from having more than one active session at a given time. If a user logs into CERF successfully, then goes to another computer and attempts to login, the individual is informed that there is already an active session at another (named) IP address. They can choose to log onto a new CERF session, which after proper credentials forcibly closes the previous session, or they can return to the other computer. All of these transactions are logged and available for monitoring and reporting by the administrator, who can investigate any unauthorized CERF use or attempted use, and can present these reports to organizational management. Additionally, a separate log called the access log displays all unsuccessful login attempts allowing administrators to determine if the attempt involves a legitimate username. |
| 11.300(e) | Initial and periodic testing of devices, such as tokens or cards, that bear or generate identification code or password information to ensure that they function properly and have not been altered in an unauthorized manner. | Not Applicable | CERF user authentication does not currently use devices or tokens for user identification. Customers with a specific requirement for special physical identification devices can request Lab-Ally consulting and customization services. |
To download a PDF version of the 21CFR11 Compliance chart for CERF above, click here.
